
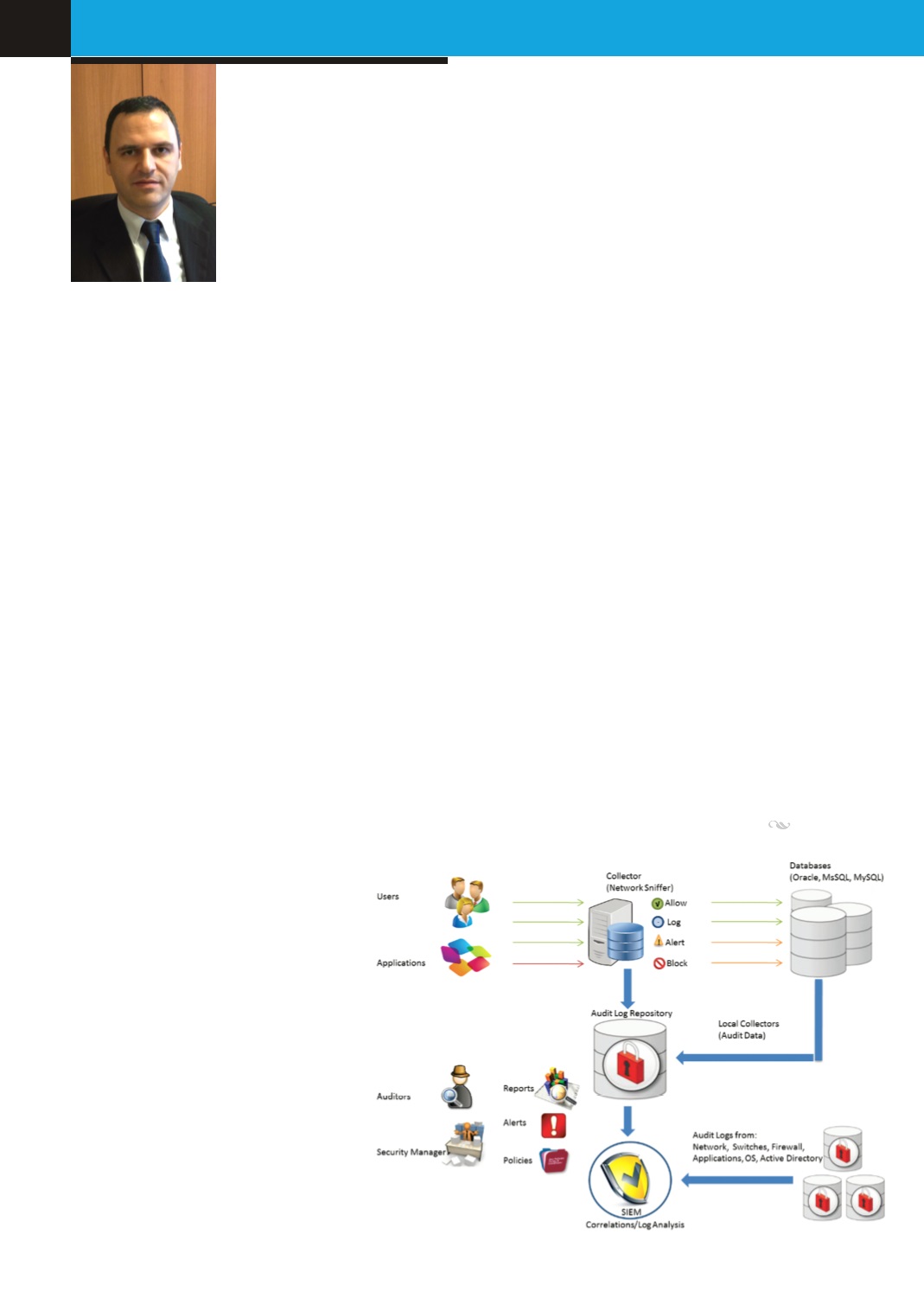
At the same time, limiting data access and logging
operations are precautions that should be applied as a
solution.
In this context, log management is given the highest
priority by Insurance Information and Monitoring Center.
By applying a special log management solution on the
database, administrators and end user actions will be
monitored, they will be analyzed with logs from other
systems, and correlations will be made with Security
Information and Event Management solution ‘SIEM’ to
produce significant relevant results. Log types which will
be basically monitored are:
Security logs: Log-ins with wrong passwords, lock of user
identity, new password requests, etc.
Transaction logs: End user activities, authorized
user activities, system administrator activities, user
creation-deletion, data interventions, etc.
Increase in digitalization and networking, particularly in
terms of “data” concept, which had been pretty ignored in
the past, is now the most valuable asset in today’s business
world. The role of data, within the privacy and quality
concept, is growing day by day and institutions who use
“data” more functionally get one step ahead in competition.
With the advances in technology, business world can now
perform things once they could never imagine; however, it
must never be forgotten that hackers also use more creative
technological methods. In parallel with changes; asocial,
young hackers have now left their places to organized
hacker teams with high damage capacities, who work
professionally for private bodies, attacking their targets with
great concentration.
This new approach of new generation
hackers caused troubles for many countries
and international giant companies in
recent years, and revealed the method of
target-based attacks (Advanced Persistent
Threat, APT) adopted by hackers.
Also, with widespread use of mobile
internet access and rapid growth of
broadband mobile networks; office and
business hours concept has become a
bit outdated. For employees, data can be
accessed anytime, anywhere now. Briefly,
for employees, anywhere with a tablet
computer, smart phone and laptop is an
office where they can continue their work
from where they left.
Considering all such risks, the first step
for providing data security is to increase
corporate Information Security awareness.
Data Security and Log Management
CISA
,
Information Security and
Risk Manager
(SBM)
İlyas
KAYMAKÇI
INFORMATION SECURITY
32
















